Phishing by Samsung’s vulnerable SES (Samsung Experience Services)
Part 1: How Samsung Users Got Played—and Why It’s Terrifying
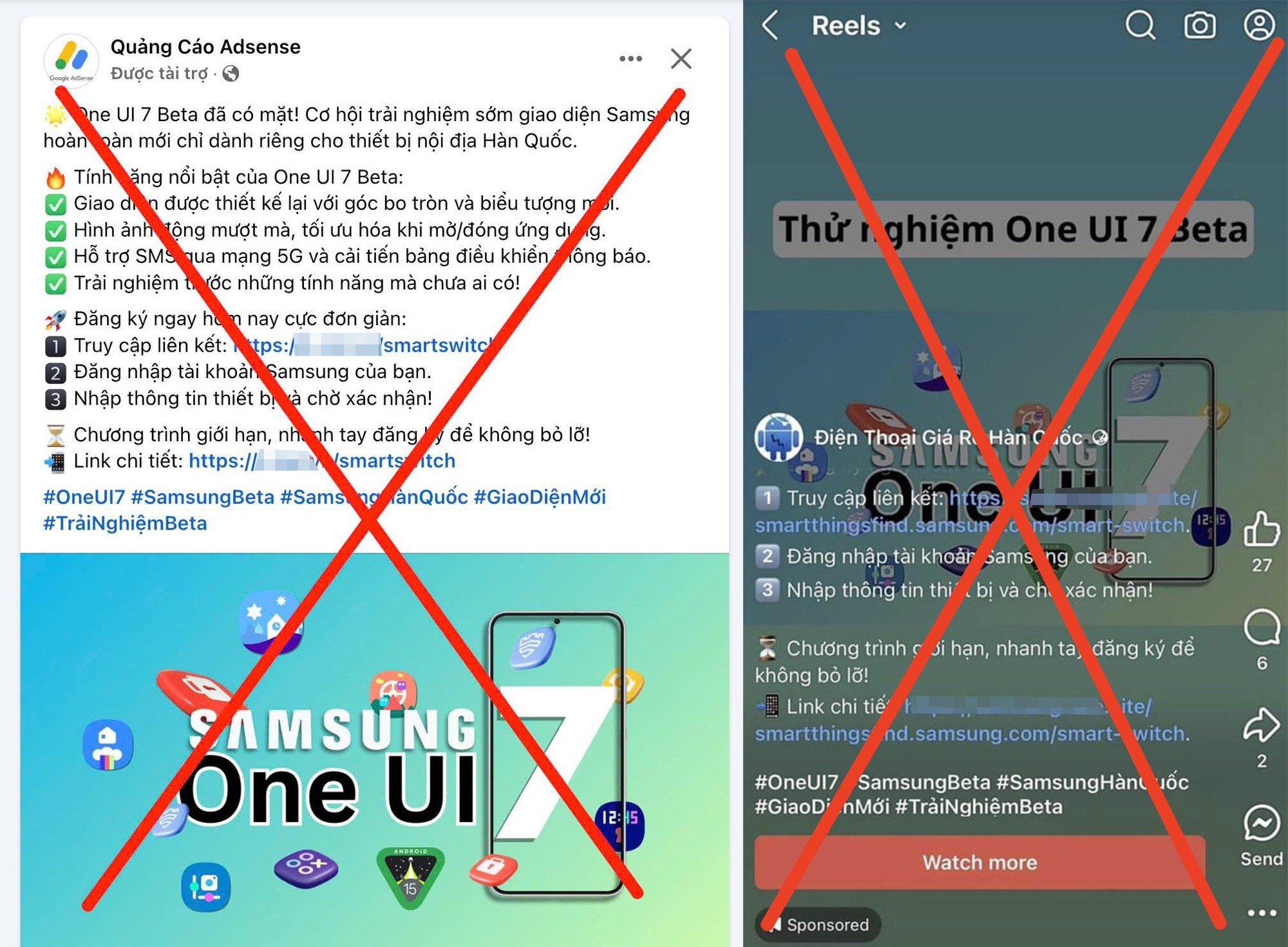
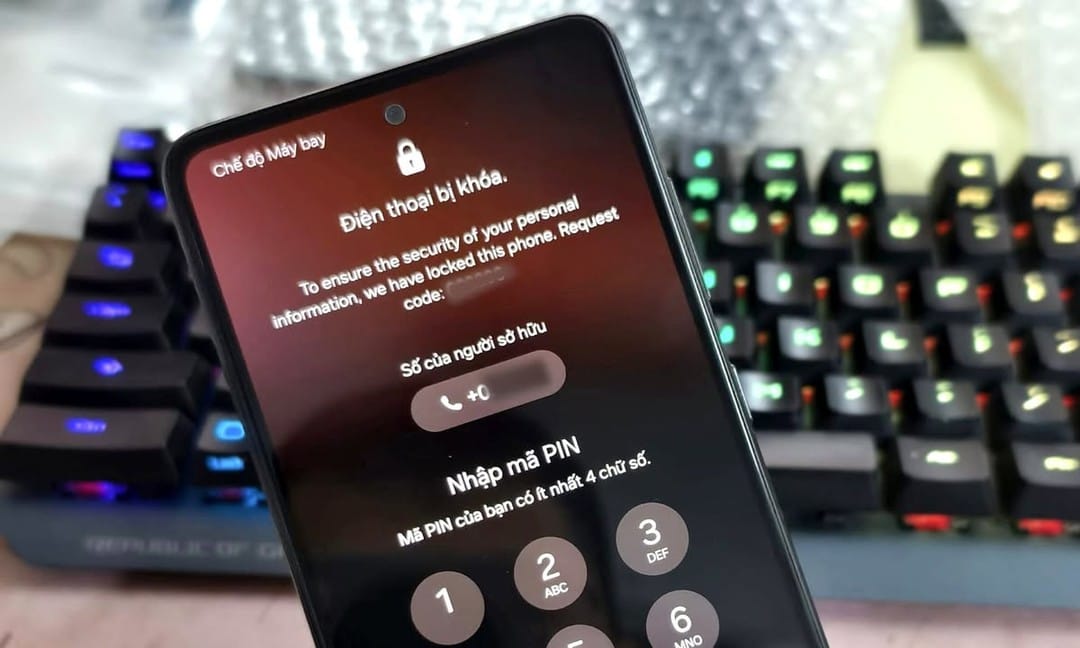
Thousands of Samsung users, hyped for One UI 7 Beta, clicked a sketchy link promising early access. It showed a popup saying "Login with Samsung," "Login to SmartThings to continue," and you clicked in. After a few days, your phone got bricked.
“Sure, blame the victims for clicking!” you might say. But hold up. When I watched those jaw-dropping victim videos, my gut screamed: “This isn’t just user error!” Two things blew my mind:
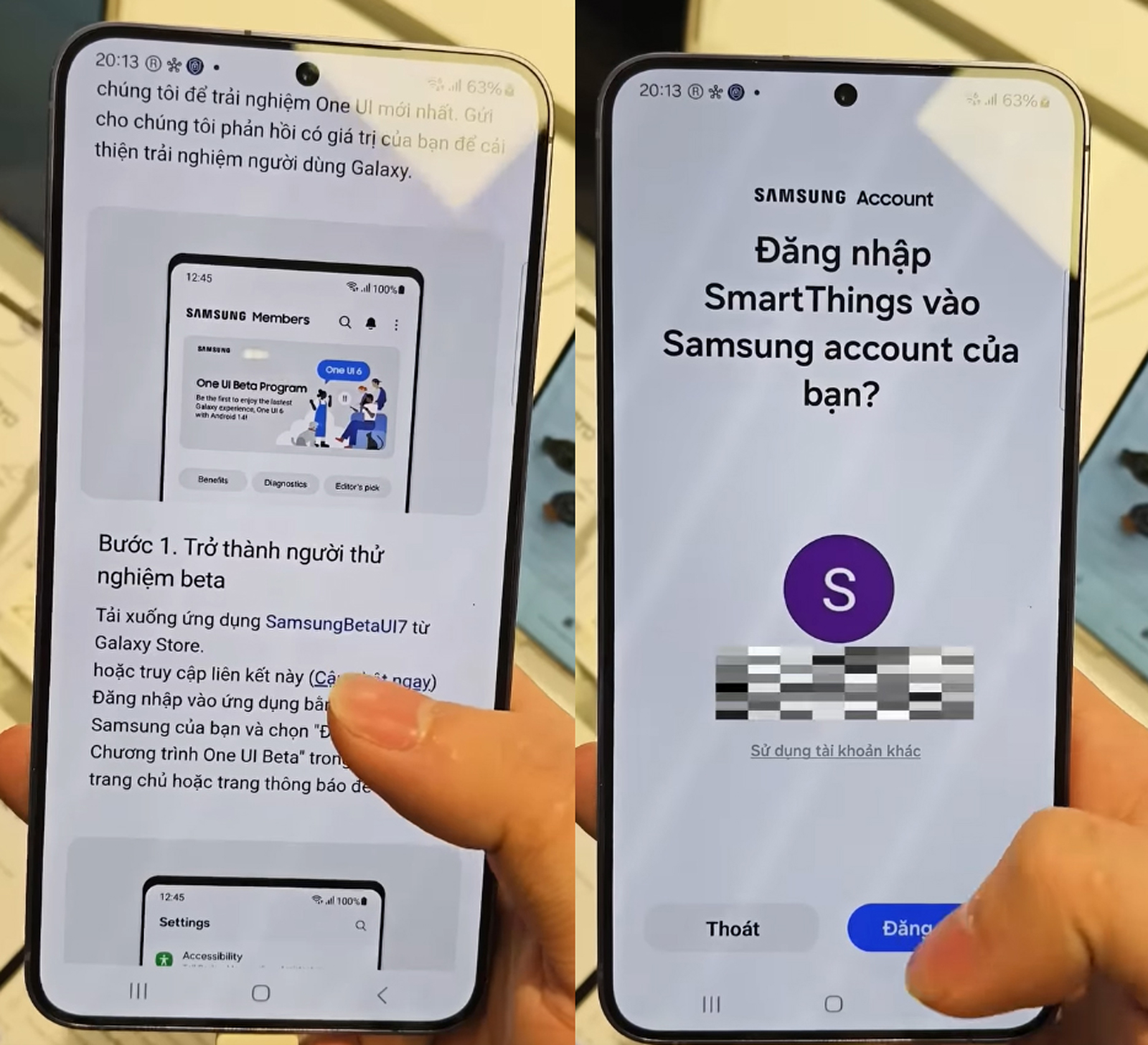
- Why did the login page LOOK EXACTLY like Samsung’s SmartThings portal?
- Why the HELL wasn’t a password required?!
By the time I dug in, the phishing site was gone. I'm using Facebook Link Debugger and Bing’s Cached Search (shoutout to Bing for once because Google had killed this service), I scraped the scam site’s code. Let me tell you—this wasn’t amateur hour.
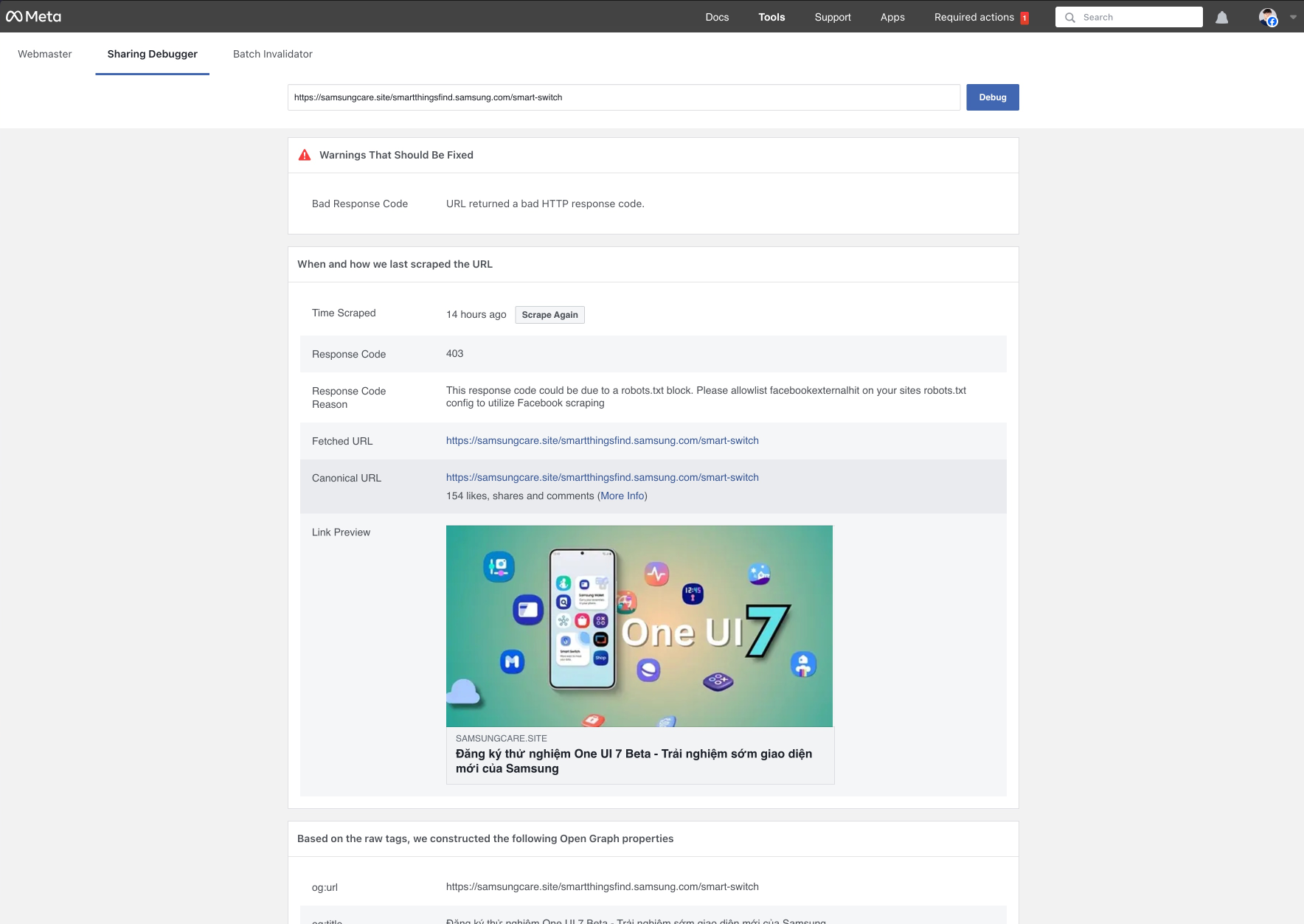
The attackers obfuscated EVERYTHING.
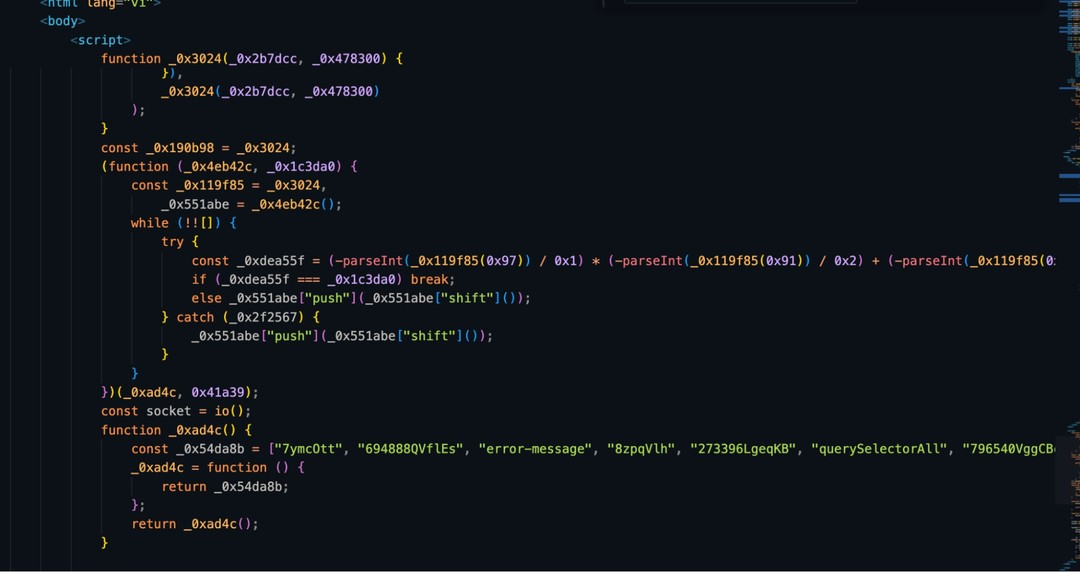
Scripts? Gibberish. HTML? A nightmare. I threw ChatGPT and Gemini at it (free 1M tokens), and finally the code unraveled.
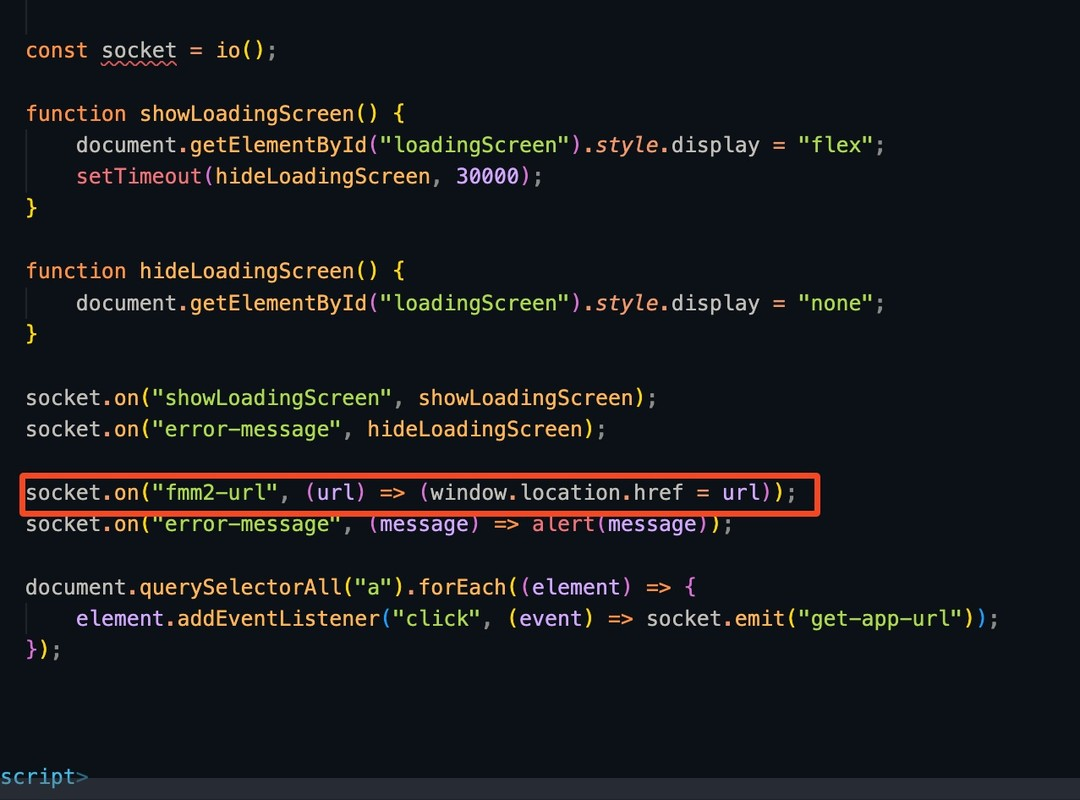
Here’s the kicker: When victims clicked the link, the site return some link to redirect them. But when I do this research the server was dead, so I couldn’t track the path—except for one keywords: FMM2.
FMM2: The “Find My Mobile” Nightmare
FMM2 (Find My Mobile) is Samsung’s “lost phone” lifeline. Normally, it lets you remotely lock/wipe your device without 2FA—but only if:
- You have the password.
- You’re a “trusted contact” (like your own devices).
But wait—here’s the terrifying: Once you log in via FMM2, the session permissions are WIDE OPEN. Attackers aren’t just locking your phone—they’re accessing SmartThings, Samsung Health, even your account settings! What the actual—?! It’s not what I looking for but wtf?
Think about this, the whole mechanism lets users log in to Find My Mobile without any 2FA. It helps them lock the phone, but after logging in, they allow them to do a lot more than that? (Samsung SmartThings, ... even Samsung Drive if Samsung had one I think)
The OAuth Trap: How Did a Phishing Site Spawn a Legit Samsung Login?
Victims saw Samsung’s official Password-less Login window. Two theories:
- Samsung’s OAuth Redirects Were a Mess
With 50+ services (SmartThings, Members, Health, etc.), even one misconfiguredredirect_uri(like allowinghttps://*) would let attackers hijack login flows. - The RCE in Samsung phone
Maybe but it's hard and I don't think attackers actually can do that.
But nothing worked and then I found this feature "QR Code Login"
QR Code Login: The Backdoor Nobody Saw Coming
Samsung’s “Login with QR Code” was the Achilles’s heel. QR code content itself is a functional link, not a code, and this is a flaw. No expire, no rolling, no nothing. What if they use the link without scanning the actual QR?
The PoC
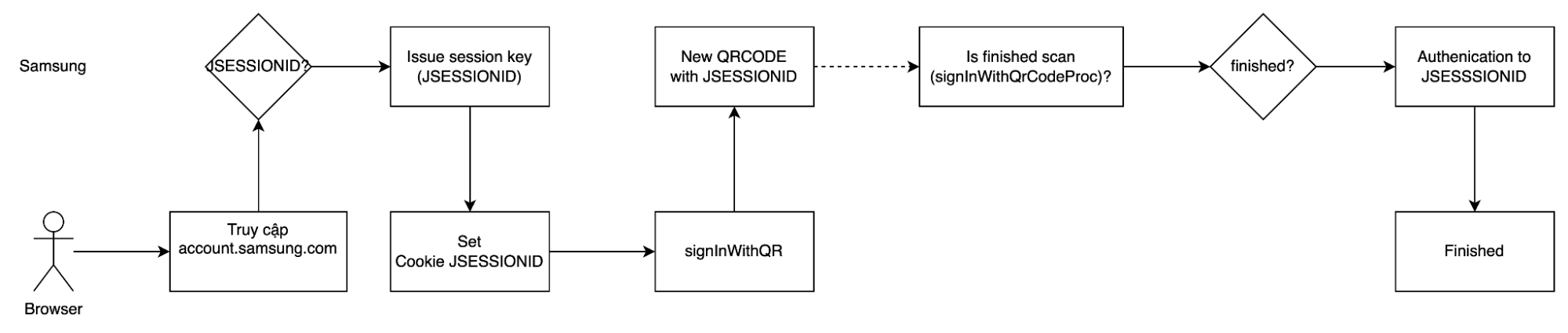
So I did make the PoC for this:
- I'm using Undetectable Chromedrive. Create Selenium - Chrome profile, go to Samsung Accounts, click on Sign in with QR code and Samsung would give me a code
- Send back that link/code to users something like "intent://signin.samsung.com/key/xxxxxx"
- Wait for them to log in. After they did, I could access their accounts.
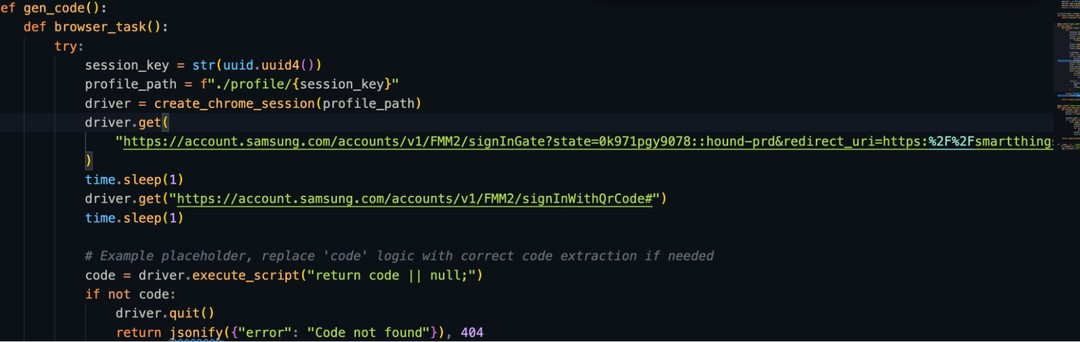
Side chat:
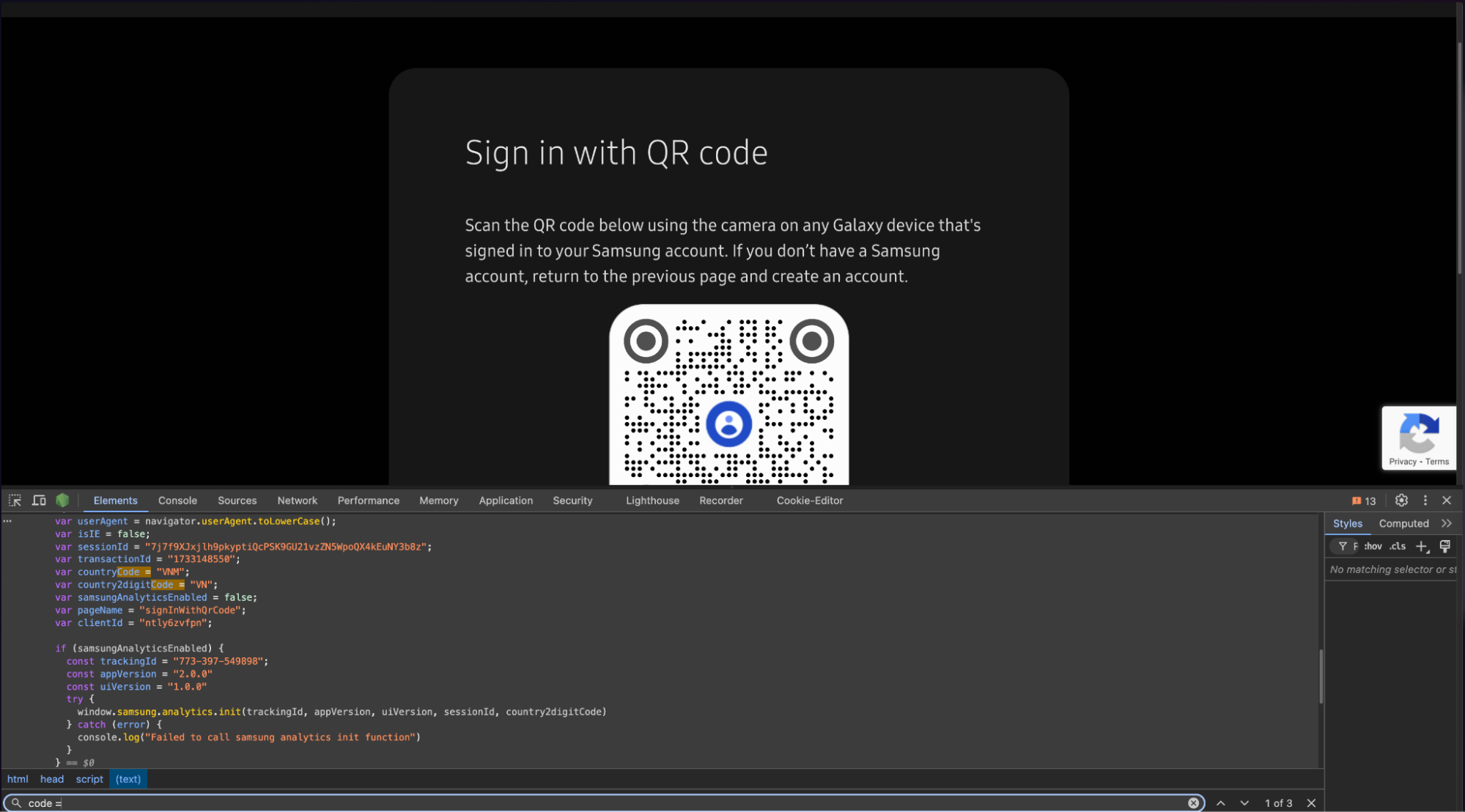
Samsung even makes the code in their script SSR something like "var code = "<?php echo $code;?>" so I just return code to get it 😂. For something like this I expect Samsung obfuscated it or made it harder to automate it but no it's not
I tested it on my Z Fold 3 (One UI 6.1.1). Holy moly—scanning a malicious QR code auto-opens a URL that triggers Password-less Login. After login, window.close() dumps users back to the PHISHING SITE, not Samsung’s portal and you know you can change the title, description of that windows like "Login to Smartthings" instead of "Remote login on another device?"
intent://signin.samsung.com/key/xxxxxx? modelName=SmartThings#Intent;scheme=https;package=com.osp.app.signin; 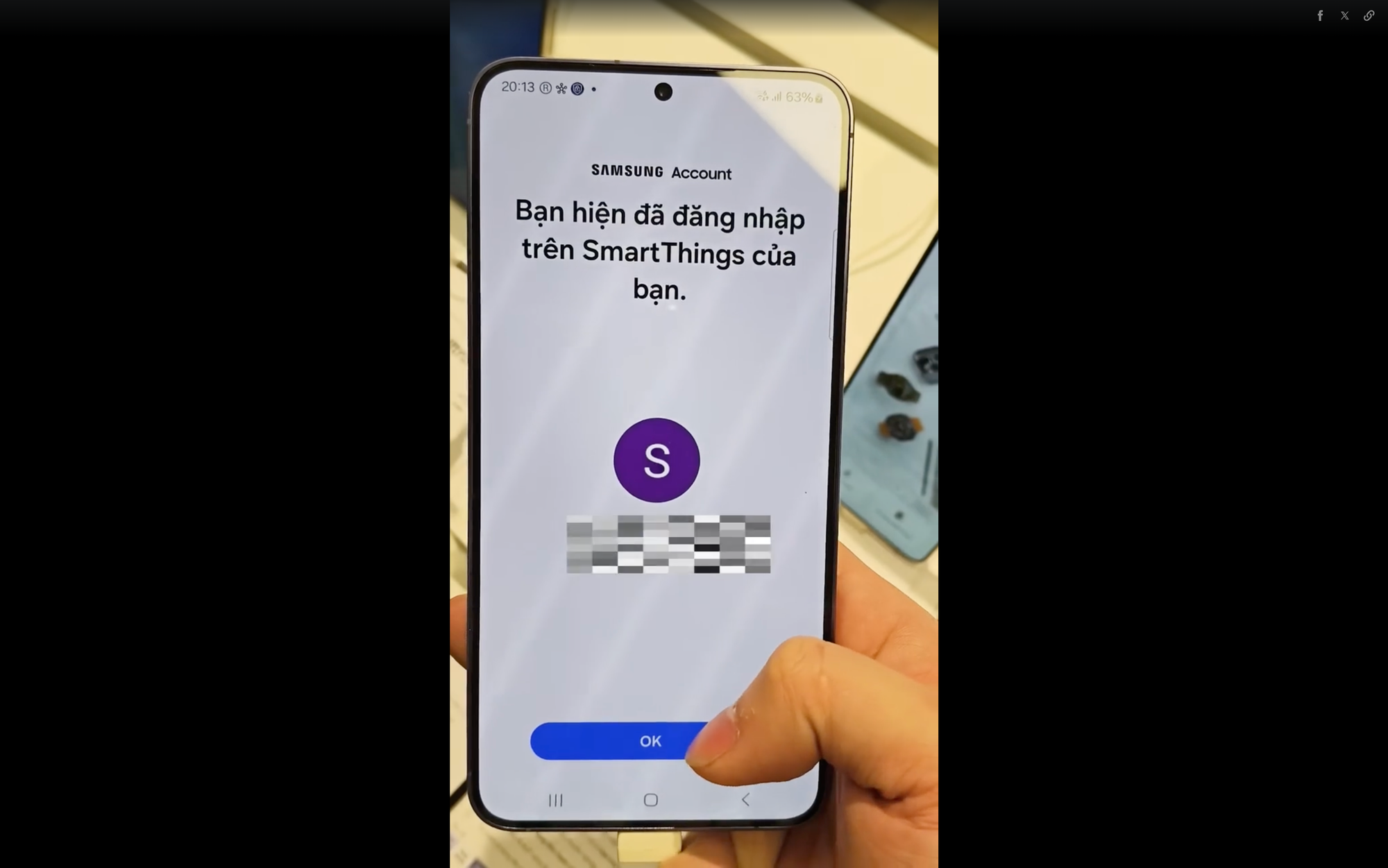
GENIUS. EVIL. TERRIFYING.
“It’s Not a Flaw!”—But Oh, It Is
“Users clicked the link—their fault!” Here’s why:
- FMM2’s permissions are WILDLY OVERREACHING. Why can a “lost phone” session access SmartThings or account settings?
- No 2FA bypass warnings. Users think they’re logging into a beta—not handing over their digital life.
- QR Code Login = No user consent. The feature auto-triggers without any “Are you sure?” prompt.
- Samsung Experience Service flaw. There is a flaw when anyone can modify the display content of Samsung Passwordless login, which can lead to confusing and phishing.
Knox Knock Knox
And then all the Samsung users had been locked out of their phones. The problem is they cannot log back to their Samsung accounts because they need 2FA, and the SIM card is in the phone (eSIM). And some of them bring their phones to Samsung Support Centre, and they said nothing they could do?!? Why? Knox had locked down the device at the hardware level, so even Samsung cannot do anything.
just wow
The Hidden Bomb: Samsung’s Domain Chaos
Samsung runs country-specific promo sites (quatangsamsung.vn, samsung-offers.in). Legit? Sure. But they’re identical to phishing traps. Example:
- Real:
vn.careplus.co(Vietnam’s promo) - Fake:
samsungcareplus.com
Why? Because Samsung hires a lot of agencies to do each part of their business, and all contractors cannot use the domain name *.samsung.com/*. They had to set up their own domain name and this led to A hundred of promos, a hundred of domain names.
The Final Twist: No Bounty but fixed 🗡️
I reported this. Samsung patched the QR loophole. But guess what? No bounty for me because of "this is a phishing attack not security vulnerable" but they had fix something to prevent this
They may right but it was a perfect storm of lax permissions, confusing UX, and corporate "things" could create a nightmare for Samsung's users.
Contact: teddie@tuta.com